If you’re like most modern IT teams, you’ve already invested in Zero Trust security for your network, cloud, and endpoints. But what about your printers?
It’s easy to forget that printers are network-connected devices, handling confidential documents and transmitting sensitive data every day. As a result, they rarely receive the same level of security attention as laptops, servers, and mobile devices.
Unfortunately, that oversight leaves your organization vulnerable, with printers becoming a weak link in your Zero Trust Architecture. Because the most robust trust Zero Trust planning extends to every endpoint, and that includes your printers.
Whether you’re managing remote printing, serverless printing, or focused on stronger printing security, the same principles apply. To bring Zero Trust to print, you need a structured approach built on four foundational pillars:
Access and identity management
Authentication for all connections and endpoints
Segmentation of data to limit breach harm
Unified security management
Let’s take a closer look at how these pillars work together to create stronger, more resilient Zero Trust security for your print environment—and your entire organization.
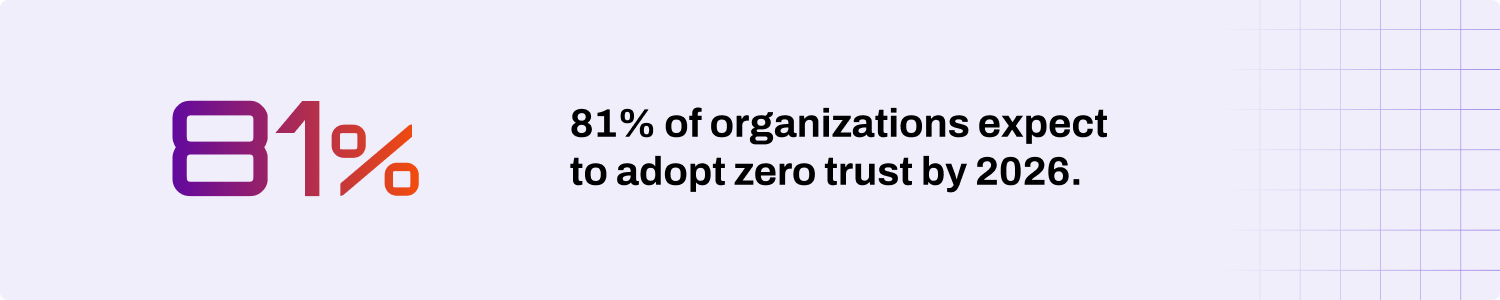
Zero Trust security is the new standard for protecting today’s organizations. By 2026, 81% of organizations expect to adopt Zero Trust, showing that more IT teams are embracing the mindset across their networks, devices, and cloud environments. Legacy printers are often a single point of failure, creating a perfect entryway for attackers. That means many organizations are still operating under the outdated assumption of trusting networks, leaving many vulnerabilities unchecked.
As hybrid and remote work continue to grow, unsecured home printers exacerbate the issue, introducing a new layer of risk as they connect to corporate networks.
Zero Trust has become imperative for print security. The core principle—“never trust, always verify”—applies to printers just as much as any other device. Every user, every connection, and every print job should be authenticated and verified before access is granted.
By extending Zero Trust to your print environment, you’re closing a critical gap, creating a security strategy that protects at every endpoint.
Zero Trust means verifying every connection, and access and identity management is where that philosophy takes shape. As the first pillar of Zero Trust printing, it ensures that only verified users can send print jobs, access printers, or manage the print infrastructure.
Access and identity management ensure that only authorized personnel can print, manage devices, or access settings. It simplifies security and eliminates vulnerabilities resulting from unmanaged or anonymous printing.
Here’s how to make it work:
Connect to your IdP: Integrate with platforms like Okta, Azure AD, or Google Identity to centralize authentication and control
Enable SSO and MFA: Let users print securely without extra passwords while adding a second layer of protection
Automate account management: Use SCIM or Just-in-Time (JIT) provisioning to automatically create, update, and deactivate accounts
The result is tighter security, fewer manual tasks for IT, and no forgotten accounts left behind to become vulnerabilities.
The need for strong identity management has never been more urgent. More than 80% of organizations experienced at least one insider-related attack in 2024, and over half of those incidents were caused by simple employee mistakes (rather than malicious hackers). Stolen credentials were involved in 22% of all breaches, highlighting just how easily attackers can gain access. And printers aren’t immune. As recently as June 2025, researchers uncovered eight critical printer vulnerabilities, including one that let attackers create default admin passwords without authentication. That’s a perfect reminder that even simple oversights can have major consequences.
And printers aren’t immune. As recently as June 2025, researchers uncovered eight critical printer vulnerabilities, including one that let attackers create default admin passwords without authentication. That’s a perfect reminder that even simple oversights can have major consequences. Most of today’s employees (83%) prefer hybrid work, meaning organizations must verify user identity regardless of where people print from—headquarters, home offices, or client sites. Centralized authentication ensures that users are validated wherever they are, maintaining consistent and secure print access across locations. Smart access management blocks threats while also simplifying control. Here are some tips for building an effective program:
Integrate with enterprise IdPs to centralize identity control
Require MFA for sensitive print actions, like secure release
Automate account provisioning and deactivation to reduce manual work
Assign role-based permissions to limit printer access by job function
Enforce strong password policies and eliminate default credentials
Conduct routine access reviews and rotate credentials to stay secure
Automating user access keeps your printers secure while making life easier for IT. Accounts are created as soon as someone joins and revoked the moment they leave. No leftover credentials, no extra work—just secure, hassle-free access that aligns perfectly with Zero Trust principles.
Pillar 2 focuses on verifying every connection, every time, leaving no room for assumptions. Unlike older “trust but verify” models, it requires checks before, during, and after each print job.
The leading Zero Trust printing solutions use direct IP printing, which changes how data moves and is protected:
Print jobs are sent directly from the user’s device to the printer
Data isn’t stored in centralized print servers or spooling systems
Every connection is individually authenticated
Print data travels across the network, but it avoids the centralized storage points that attackers typically target
This approach minimizes risk while maintaining efficiency, ensuring that even if one connection is compromised, the rest of the system stays secure.
Traditional print servers can be a serious weak spot in your network, creating multiple opportunities for attackers to exploit:
Centralized print job storage is an easy target for attackers
Multiple devices connecting through a single server increases exposure
Cached data and persistent network connections remain at risk.
A compromise of a single server can expose all connected users’ print data
Recent events show just how real these threats are. Windows Print Spooler vulnerabilities prove that attackers are still actively targeting print infrastructure. And while Microsoft’s monumental launch of Windows Protected Print (WPP) addresses many of these vulnerabilities, strong, continuous authentication is still essential to keep printers and networks secure. Building robust authentication into your print environment is essential for keeping sensitive documents and data safe, and it doesn’t have to be complicated. Here’s how to reduce risk while maintaining smooth operations for your team:
Implement certificate-based authentication for printer connections where supported
Use TLS/SSL encryption for all print traffic
Verify device compliance before allowing print access
Monitor and log all authentication attempts
Disable or remove default/anonymous access
Deploy print solutions that support secure authentication across multiple device types
Zero Trust printing isn’t just for laptops sitting at your desk. Today’s solutions enable you to authenticate print jobs from mobile devices, tablets, and other endpoints, ensuring consistent security regardless of how or where employees are printing.
For print environments, segmentation is crucial in preventing compromised devices from accessing other systems or sensitive data across your network. By breaking your infrastructure into isolated zones, you can limit exposure and reduce the impact of any potential breach.
Segmentation means creating strategic boundaries that make it much harder for attackers to move freely or access sensitive data. There are two main ways to do this:
Network Segmentation (Microsegmentation): Divides your network into small, isolated zones. In print environments, this means isolating printers on dedicated network segments with controlled access points, so a compromised device can’t easily reach other resources.
Architectural Segmentation (Serverless Printing): Eliminates centralized print servers, allowing direct device-to-printer connections. While related to microsegmentation, it’s an architectural choice that reduces centralized points of failure.
Note: It’s not all or nothing. You can implement network segmentation even with print servers in place, and you can also adopt serverless printing without full network segmentation. Both approaches enhance security—but combining them gives you the strongest protection.
Segmentation is vital for keeping breaches from getting out of control. Most organizations (about 96%) use some form of network segmentation, but very few (around 2%) have thoroughly segmented all their mission-critical areas, including printers. That means printers are often among the least protected systems, leaving them vulnerable to potential attacks. Proper segmentation helps close that gap, making it easier to contain breaches when they do occur. In fact, IBM research found that organizations that contain breaches in under 200 days save an average of 29%, translating to about $1.14 million per incident. Implementing segmentation is where Zero Trust really starts to pay off. Here are the concrete steps you need to protect your printers and reduce risk:
Network-Level Segmentation:
Place printers on isolated network segments or VLANs
Separate print traffic from general network traffic
Implement access control lists (ACLs) at network boundaries
Restrict unnecessary printer-to-printer communication
Apply Zero Trust network access (ZTNA) principles to print traffic
Architectural Approaches:
Eliminate or reduce dependence on centralized print servers where feasible
Use direct device-to-printer connections
Implement secure cloud-based print management where appropriate
(Even if your organization still needs print servers for certain legacy applications or workflows, you can still apply Zero Trust principles using other security controls.)
Data Protection Strategies:
Encrypt print jobs in transit and at rest
Implement automatic data deletion policies after job completion
Use secure release printing to prevent sensitive documents from sitting in output trays
Ensure printer hard drives are encrypted or regularly wiped
User-Level Access Controls:
Implement role-based printer access
Separate guest printing from employee printing
Create department-specific print queues with appropriate access controls
Limit access to high-security printers (check printing, confidential documents)
If a device gets compromised, proper segmentation keeps the problem from spreading. Attackers can’t use your print system to reach other users’ data or move throughout the network. Instead, the breach stays contained to that single endpoint, keeping both your printers and the rest of your network safe.
Even if your print environment is spread out and centralized servers are minimized or gone, your security management shouldn’t be scattered. That’s where the fourth pillar comes into play.
Keeping oversight centralized enables IT teams to view and manage every printer, user, and print job from a single platform, thereby eliminating another potential point of failure. A strong centralized platform should make it easy to:
Assign admin roles with role-based access control (RBAC)
Keep detailed audit logs of all print activity
Monitor activity in real time and get alerts for unusual behavior
Automate policy enforcement across all printers and users
Manage firmware updates and patches centrally
Maintain consistent security configurations across your distributed environment
With these tools in place, your team can manage a distributed print environment as efficiently as a single, centralized system.
Visibility is crucial, especially for teams facing security skill shortages. IBM research shows that organizations with high skills gaps face average breach costs of $5.22M—43% higher than those without gaps. Centralized management and automation enable even smaller IT teams to maintain tight security without feeling overwhelmed. Including printers in your audit and compliance strategy makes IT tasks easier, too. Even if regulations don’t specifically call out print systems, tracking print activity demonstrates comprehensive control and helps meet standards in industries like healthcare (HIPAA), finance (SOX), and government.
Unified security management works best when it’s practical and actionable. Here’s how to make it work for your print environment.
Monitoring and Auditing:
Log all print jobs with user, device, printer, timestamp, and document metadata
Track administrator configuration changes
Monitor for anomalous printing behavior or policy violations
Generate compliance reports automatically
Integrate with SIEM systems where appropriate
Delegated Access Control:
Assign administrative roles based on job function and need
Allow power users to manage their department's printers within defined boundaries
Enable secure self-service printer installation where appropriate and properly controlled
Restrict sensitive printer access to authorized personnel only
Security Enforcement:
Secure Release Printing: Jobs are held at the printer until the user authenticates at the device
Pull Printing: Jobs follow users to any approved printer after authentication
Off-Network Printing: Secure printing for remote workers, ideally without requiring VPN connections
Encryption: Enforce encryption for all print data in transit and at rest
Policy Templates: Pre-configured security policies for different user groups or document types
With unified security management, IT teams can manage driver updates, configurations, and policies from a single central console. Self-service features enable users to resolve minor issues independently, reducing helpdesk requests. At the same time, centralized monitoring provides teams with clear visibility into the environment, making it easier to identify and address problems before they escalate.
The four pillars of Zero Trust printing don’t work in isolation. They’re part of a connected strategy that keeps your print environment secure from end to end:
Identity Management: Verifies who can print
Authentication: Checks every connection and transaction
Segmentation: Limits potential damage if something goes wrong
Unified Management: Enforces policies, monitors activity, and audits continuously
Take a real-world example: when a remote employee prints a confidential document, they first authenticate through corporate SSO with MFA (Pillar 1). Their device then creates a secure, encrypted connection directly to the printer (Pillar 2). The data bypasses shared storage, and network segmentation ensures that even if their device is compromised, attackers can’t move within the system (Pillar 3). Meanwhile, IT sees the activity in real time, confirms policy compliance, and can audit or investigate any anomalies (Pillar 4).
The result is a print environment that’s both secure and efficient. Employees can complete their work without friction, while IT maintains control, visibility, and confidence that Zero Trust principles are applied at every step.
Starting a Zero Trust printing program doesn’t have to feel overwhelming. Begin with a thorough assessment:
Inventory all printers and multifunction devices
Document current authentication methods and identify weak points
Map print servers and centralized infrastructure dependencies
Review printer access patterns by user role and department
Identify compliance requirements for audit trails and data protection
Assess network segmentation of your print infrastructure
Next, prioritize the highest-risk areas, such as:
Printers handling confidential data (HR, Finance, Legal, Executive)
Remote worker printing scenarios
Guest and contractor printing access
High-value printing like checks, credentials, or sensitive documents
Departments subject to regulatory compliance
Finally, outline an implementation roadmap to put your strategy into action:
Integrate with your existing IdP and enable SSO (Pillar 1)
Implement MFA for print release and administrative access (Pillars 1 and 2)
Assess and improve network segmentation for printers (Pillar 3)
Deploy modern print architecture, considering serverless where appropriate (Pillar 3)
Implement a unified management platform with comprehensive logging (Pillar 4)
Phase out unnecessary print servers gradually (Pillar 3)
Establish continuous monitoring and improvement processes (Pillar 4)
This approach helps you secure your print environment methodically, tackling the riskiest areas first while building a sustainable Zero Trust framework.
Your Zero Trust architecture isn’t complete unless it includes print. This oversight is both risky and costly for your organization: 67% of organizations experienced printer-related security incidents in 2024, and 74% of SMBs reported data loss through print systems.  Fortunately, the four-pillar framework provides a clear and practical approach to bridging the gap. So take action today. Begin by assessing your current print environment to identify gaps, then build a roadmap to secure every endpoint. Modern solutions like Vasion Print make this easier, giving IT teams centralized control, monitoring, and enforcement across distributed print environments.
Fortunately, the four-pillar framework provides a clear and practical approach to bridging the gap. So take action today. Begin by assessing your current print environment to identify gaps, then build a roadmap to secure every endpoint. Modern solutions like Vasion Print make this easier, giving IT teams centralized control, monitoring, and enforcement across distributed print environments.Discover how enterprise-grade Zero Trust printing can be implemented in your organization. Schedule a demo today. 

 And printers aren’t immune. As recently as June 2025, researchers uncovered eight critical printer vulnerabilities, including one that let attackers create default admin passwords without authentication. That’s a perfect reminder that even simple oversights can have major consequences.
And printers aren’t immune. As recently as June 2025, researchers uncovered eight critical printer vulnerabilities, including one that let attackers create default admin passwords without authentication. That’s a perfect reminder that even simple oversights can have major consequences. Implementation Best Practices
Implementation Best Practices Fortunately, the four-pillar framework provides a clear and practical approach to bridging the gap. So take action today. Begin by assessing your current print environment to identify gaps, then build a roadmap to secure every endpoint. Modern solutions like Vasion Print make this easier, giving IT teams centralized control, monitoring, and enforcement across distributed print environments.
Fortunately, the four-pillar framework provides a clear and practical approach to bridging the gap. So take action today. Begin by assessing your current print environment to identify gaps, then build a roadmap to secure every endpoint. Modern solutions like Vasion Print make this easier, giving IT teams centralized control, monitoring, and enforcement across distributed print environments.