Why Zero Trust Matters for Print Management


Vasion Team
November 19, 2025
5 mins
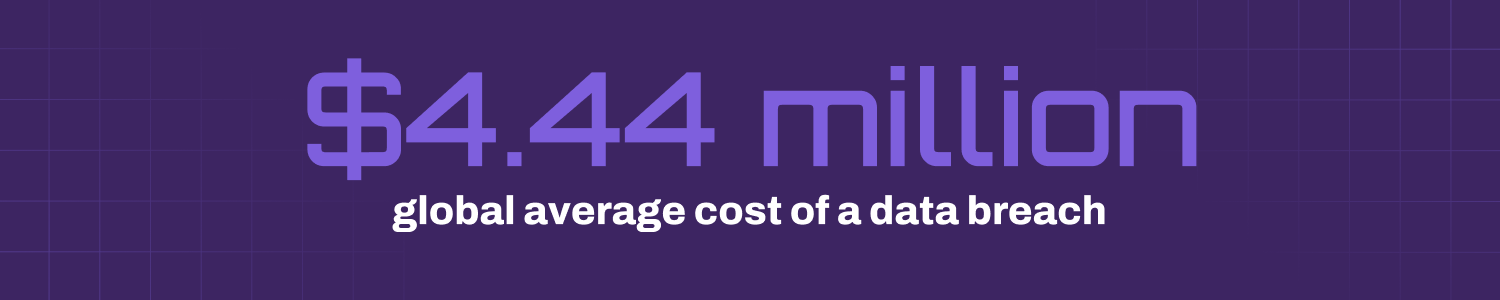
In an era where cyber threats are escalating and data breaches are increasingly costly, no aspect of IT infrastructure can be ignored, including printing. According to IBM’s Cost of a Data Breach Report 2025, the global average cost of a data breach has reached $4.44 million, underscoring the growing financial risk of inadequate security. Meanwhile, research from Quocirca reveals that 67% of organizations experienced printer-related security incidents in 2024, up from 61% the year before. This rise clearly shows that print environments remain a vulnerable gap in enterprise defenses.
The shift to remote and hybrid work has only compounded the challenge. With 32.6 million Americans, or 22% of the U.S. workforce, working remotely in 2025, employees now use remote printing from home networks and mobile devices outside traditional security perimeters. Legacy “castle and moat” security models can no longer keep pace with the dispersed and flexible work environments of today.
That is why organizations are turning to Zero Trust Architecture. It is no longer just for network access but is now essential for print management, one of the most overlooked yet high-risk components of modern IT security.
Understanding Zero Trust Architecture
At its core, Zero Trust is built on a simple principle: “never trust, always verify.” Instead of assuming that users or devices inside the network are safe, every access request must be continuously authenticated, authorized, and encrypted.
What Zero Trust Is—and Isn’t
As John Kindervag, the former Forrester analyst who pioneered the concept, famously said, “Zero Trust is not a product—it’s a complete security shift.”
Zero Trust is not a single product or quick fix. It’s a holistic framework that redefines how organizations secure their systems, users, and data. The model assumes that threats can originate from anywhere—both inside and outside the network—so no device, application, or user is automatically trusted. This approach replaces the traditional perimeter-based “castle and moat” model, which breaks down in today’s hybrid and remote work environments where data moves fluidly across devices, clouds, and geographies.
Core Principles of Zero Trust Security
Implementing Zero Trust requires adherence to several foundational principles. The Principle of Least Privilege (PoLP) restricts access rights to only what’s necessary for a specific role, reducing the potential damage of compromised credentials. Microsegmentation divides networks into smaller, controlled zones to prevent lateral movement by attackers. And perhaps most importantly, Zero Trust eliminates default trust. No device or user is inherently safe until proven otherwise.
Why Zero Trust Adoption Has Accelerated
The shift toward remote and hybrid work has made Zero Trust essential. Today, 83% of global employees prefer hybrid work arrangements that blend flexibility with collaboration, increasing the need for secure, adaptable access across multiple environments. With the rise of remote work, BYOD policies, and sophisticated ransomware, the Zero Trust model is quickly becoming the global standard for safeguarding modern infrastructure, including print environments.
Organizations adopting Zero Trust often pair it with AI and automation, which deliver measurable results. The IBM Cost of a Data Breach Report 2025 found that companies using AI and automation in their security stack—both common components of modern Zero Trust frameworks—save $1.9 million per breach and detect threats 80 days faster on average.

The Hidden Vulnerability: Print Infrastructure
Print infrastructure is often treated as a benign, low-risk part of IT. That’s a mistake. Printers frequently outlive other office hardware (typically 3-5 year lifespans) yet are rarely updated or patched during their whole lifecycle. This makes them a persistent weak link in enterprise security.
In fact, according to Quocirca’s Print Security Landscape 2024, 67% of organizations reported experiencing data loss incidents related to printing in the past year, up from 61% in 2023. Meanwhile, 74% of small and mid-market organizations admitted to printer-related data loss over the same period. These numbers underscore the underestimation of print as a potential attack vector.
Real-World Print Security Incidents
Print vulnerabilities are not theoretical. In June 2025, security researchers uncovered eight critical vulnerabilities affecting 748 printer models across five vendors (Brother, FUJIFILM, Ricoh, Toshiba, Konica Minolta). The worst, CVE-2024-51978, carries a Common Vulnerability Scoring System (CVSS) score of 9.8 for authentication bypass. For context, a CVSS score ranges from 0 to 10 (with 10 being the highest) and gauges a software’s vulnerability and the potential threat to impact an organization. That means the eight critical vulnerabilities uncovered by researchers posed an extremely high risk to those major companies.
The Print Server Problem
Print servers are another Achilles’ heel. As the central hub for print job routing, they become a single point of failure and a practical attack vector.
The increasing complexity of managing mixed fleets, patches, drivers, and ongoing print server maintenance adds further strain on IT teams and widens the window for potential breaches. Compromise techniques include malicious driver installation, spooler file exploits, or remote code execution through known flaws in print service protocols.
Organizations are starting to take action against the constant frustrations of print servers. One prominent example is Microsoft, which introduced Windows Protected Print (WPP) in October 2024. The new platform aims to harden driver attacks and patch vulnerabilities in the print path. Not only is WPP the most substantial change to the Windows print stack in over two decades, it’s also an industry-changing move toward secure, driverless print environments. WPP represents a significant shift away from traditional client-server print architectures, rendering print servers less relevant as printing becomes increasingly secure at the endpoint level.
Remote Printing Compounds the Risk
Remote work introduces additional exposure. Many remote employees still require printing, often using home printers connected to corporate devices. Quocirca’s research shows organizations are carrying serious concerns about home printing security.
Two high-risk attack vectors in such environments:
- Home printers without proper Zero Trust security can bypass VPNs or corporate network protections, exposing print traffic directly.
- Sensitive data stored on printer hard drives or caches may be accessible if the home Wi-Fi or the printer’s embedded OS is compromised.
Together, these vulnerabilities make print infrastructure a stealth portal into enterprise networks—one that rarely gets the attention it deserves.
Benefits of Zero Trust Print Security
Zero Trust print security transforms print environments from unmanaged vulnerabilities into tightly controlled, intelligent ecosystems. By applying the “never trust, always verify” principle to every print interaction, organizations can secure one of their most overlooked data channels while improving efficiency and resilience.
Operational Benefits
Zero Trust printing strengthens protection for remote and hybrid workers by ensuring that every print request is authenticated and encrypted before release. It simplifies print management for IT teams by automating access controls and removing reliance on vulnerable print servers. Companies also benefit from reduced attack surfaces across locations and improved scalability without the infrastructure bloat that comes from maintaining multiple print servers.
Financial Benefits
The financial case for Zero Trust is compelling, especially considering it can reduce data breaches. According to the IBM Cost of a Data Breach Report 2025, the global average cost of a data breach fell to $4.44 million in 2025, a 9% drop from 2024’s record high. However, in the U.S., it soared to an average of $10.22 million. Companies with strong security skills avoid average breach costs of $3.65 million, compared with $5.22 million for those facing shortages. Zero Trust principles help reduce breaches and avoid fines.
Security and Compliance Benefits
Zero Trust enhances threat detection, improves visibility into all print activity, and ensures better compliance with global data protection laws. It provides stronger audit trails, greater accountability, and peace of mind that every print action is securely governed.
Overcoming the Hurdles to Zero Trust
For many organizations, implementing Zero Trust can seem daunting. Budget limitations, legacy infrastructure, and uncertainty about where to begin often slow progress. However, Zero Trust doesn’t have to mean an immediate, expensive overhaul. It’s about building security maturity over time.
Challenge 1: Limited Budgets
Not every organization can replace its entire stack at once. The key is to leverage existing technology and integrate Zero Trust principles into what you already have, adding new tools only where necessary.
Challenge 2: Resistance To Change
Adopting Zero Trust can meet internal pushback. Focus on incremental improvements, not rip-and-replace strategies. Small wins, like securing your print infrastructure, build confidence and momentum.
Challenge 3: Understanding Critical Steps
Knowing where to apply Zero Trust first is crucial. Start with high-risk areas like print infrastructure, which are often overlooked yet highly vulnerable.
Challenge 4: Not Knowing Where To Start
If you’re unsure how to begin, conduct a Zero Trust printing assessment to evaluate your current risks and create a roadmap for improvement.
Zero Trust is a journey, not a destination. Begin with manageable steps, prove success, and scale as your organization’s security posture evolves.
Make Print Security the First Step in Your Zero Trust Journey
As remote and hybrid work become permanent fixtures, Zero Trust Architecture is no longer optional—it’s essential. Yet while most organizations focus on networks and endpoints, print infrastructure remains one of the most overlooked vulnerabilities in enterprise security. Every unverified device and unsecured connection represents a potential breach waiting to happen.
To keep your organization safe and prevent data breaches, here are some immediate steps your organization can take:
- Assess your current print security posture
- Identify gaps in your Zero Trust Architecture, particularly around print infrastructure
- Consider serverless printing solutions, such as Vasion Print, that support Zero Trust principles
Zero Trust printing bridges the gap between productivity and protection, ensuring that users can print securely from anywhere without exposing sensitive data. By starting with your print environment, you can quickly reduce risk, strengthen compliance, and lay the foundation for a broader Zero Trust strategy.
Take the first step toward a safer, smarter future. Discover how Vasion Print enables organizations to implement Zero Trust principles, securing every document, device, and connection without compromising performance. Schedule a demo today.
Table of Contents
Understanding Zero Trust Architecture
What Zero Trust Is—and Isn’t
Core Principles of Zero Trust Security
Why Zero Trust Adoption Has Accelerated
The Hidden Vulnerability: Print Infrastructure
Real-World Print Security Incidents
The Print Server Problem
Remote Printing Compounds the Risk
Benefits of Zero Trust Print Security
Operational Benefits
Financial Benefits
Security and Compliance Benefits
Overcoming the Hurdles to Zero Trust
Challenge 1: Limited Budgets
Challenge 2: Resistance To Change
Challenge 3: Understanding Critical Steps
Challenge 4: Not Knowing Where To Start
Make Print Security the First Step in Your Zero Trust Journey